We discuss the legal and commercial implications of the LockBit takedown, following the success of Operation Cronos.
LockBit are one of the most active ransomware groups in the world, responsible for a major proportion of global cyber-attacks and data breaches since their debut in late-2019. LockBit operate as a 'ransomware as a service' (RaaS) whereby recruited affiliates can utilise LockBit's ransomware software to target organisations across a variety of sectors and jurisdictions.
LockBit sells their ransomware software (or variants) to affiliates by taking a 20% share of any ransom payment and as an RaaS organisation, they provide affiliates with bespoke encryptors, access to LockBit's dark web leak site, and at times, assist with negotiation of ransom payments.
Over the last four years, LockBit have purportedly caused global losses in the billions (£) via ransom payments and business recovery losses. Due to the wide range of international LockBit affiliates, it is often difficult to predict their tactics, techniques and procedures (TTPs) for each individual cyber incident and as such, it is not easy for law enforcement to track down LockBit and attempt to take down their infrastructure.
Operation Cronos
On 19 th February 2024, the UK National Crime Agency (NCA) and the FBI, along with nine other international agencies, coordinated 'Operation Cronos', which involved the seizure of LockBit's leak site on the dark web and 'unprecedented' access to LockBit's systems and infrastructure.
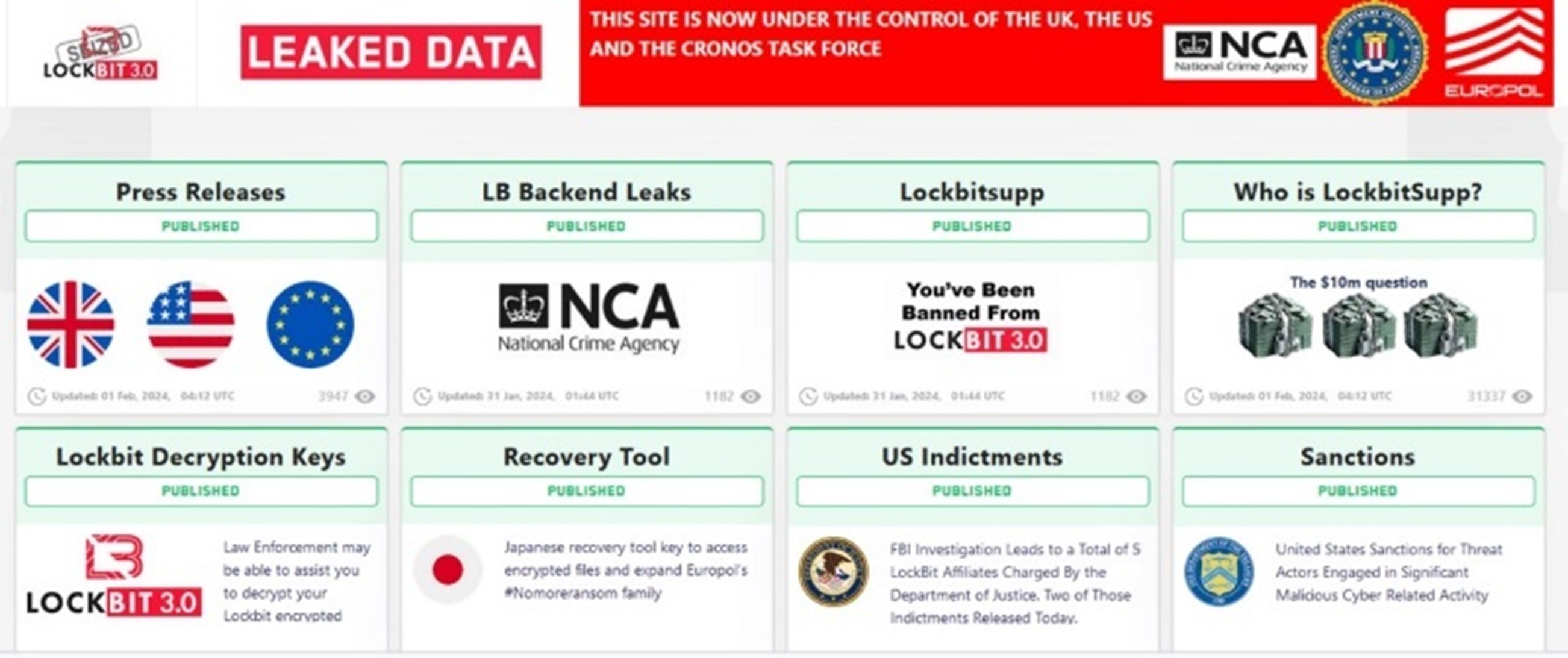
The new LockBit homepage
Following the takeover of LockBit's infrastructure and servers, these agencies were able to re-engineer aspects of the page to display the seized elements of LockBit's operation (in a similar fashion to how Police exhibit drugs or weapons). This included:
- Releasing a decryptor tool which will assist organisations who are currently or have previously been a victim of LockBit's ransomware variant.
- Seizing Bitcoin wallets linked to ransom payments.
- Producing a list of all known LockBit affiliates and bringing various sanctions, indictments and arrests against them.
- Outlining evidence that LockBit retained victim data following the payment of a ransom.
The now seized LockBit leak site
Decryptors
Law enforcement were able to obtain and release over 1,000 decryptor keys which will enable organisations who fell victim to a LockBit ransomware attack to potentially restore their systems and decrypt data and/or devices that were once thought to be unrecoverable. More on the impact of decryptors below.
Bitcoin
Law enforcement were able to freeze approximately 200 Bitcoin wallets and were able to identify that between July 2022 to February 2024, over USD $126m in Bitcoin was transferred through 30,000 accounts associated with LockBit.
Approximately USD $114m in Bitcoin remained untouched in LockBit's accounts, which was comprised of ransom payments and LockBit affiliate fees.
Arrests, Indictments and Sanctions on LockBit affiliates
Law enforcement released the identities of over 190 LockBit affiliates and their alias. Affiliates are either organisations or individuals who work directly with LockBit to target organisations around the world.
Ukrainian and Polish authorities were able to arrest three LockBit affiliates located in Poland and Ukraine and the US Department of Justice indicted and sanctioned two Russian nationals who are linked to LockBit.
Additionally, the NCA revealed that LockBitSupp , the apparent leader behind LockBit, has engaged with law enforcement and the NCA announced that they aware of his identity, where he lives and how much he is worth.
LockBit 'deleting' data following ransom payment
LockBit's extortion tactics included the theft and leak of a victim's data if a ransom was not paid. Conversely, LockBit 'promised' to delete all exfiltrated data following receipt of the ransom payment. Law enforcement were able to identify that LockBit stored the exfiltrated data from victims who paid ransoms either via share sites like mega.nz or on LockBit's own servers.
Of course, there is never any certainty as to whether a threat actor has or has not followed through with a promise to delete data. The news that LockBit did not follow through their promises will highlight that such promises by threat actors are unreliable.
LockBit resurfaces
A few days after Operation Cronos' take down of LockBit's activities, the threat actors resurfaced moving to a new dark web site and naming more victims.
LockBit announced their infrastructure and new affiliate domains have been activated, but that it would take time to rebuild their affiliate network. In a statement released on their new dark web page, they noted that some of their rivals may also be compromised and that they have instructed their affiliates to begin targeting US government institutions.
LockBit's resurfacing was not unexpected. A number of commentators had publicly down-played the significance of Operation Cronos noting that law enforcement take down efforts are the equivalent of "whack-a-mole" where the threat actors simply reappear elsewhere.
However, just because LockBit have reappeared does not make Operation Cronos a failure nor does it mean it was fruitless. Indeed, we suspect law enforcement expected LockBit to reappear elsewhere. The action against LockBit did not simply take down LockBit's leak site but also showcases the fact that law enforcement was able to obtain decryptors, freeze crypto assets, identify affiliates and applying serious sanctions on individuals. It establishes that threat actor groups are not acting with impunity, have their own vulnerabilities, and have something to lose.
What does this mean for organisations?
Our Cyber & Data Risk team as the following reflections on the implications of the LockBit takedown.
Relief for organisations
With the release of the decryption tools [1] , clients and/or policyholders who may still have unencrypted data and systems from previous or ongoing attacks by LockBit, may now rely on the released decryptor to restore their systems without having to contemplate paying a ransom or negotiating at all. We are aware that the FBI, NCA and other law enforcement authorities have been proactively reaching out to victims to offer their assistance by providing the decryptor and assisting with its implementation.
Retaining encrypted data
Obtaining a decryptor tool also begs the question for clients: how long should an organisation retain encrypted data or devices in the hope that a decryptor may become available in the future? With the success of Operation Cronos, it is evident that it is no longer a fanciful prospect that law enforcement can undertake coordinated efforts to take down threat actor groups and obtain one of the most important tools needed for organisations, a decryptor. Additionally, the fallout from Operation Cronos and future Operations, will open the discussion on whether it will be guidance and/or good practice for organisations to retain their encrypted data/devices to potentially reduce regulatory action. However, if organisations maintain sufficient backups, forensic investigators may err on the side of caution by rebuilding the victim's network and wipe / re-use encrypted drives or devices, rather than keep them dormant, to get an organisation up and running quickly and efficiently.
Regulators
It will be interesting to see how regulators in the UK and other jurisdictions will alter their views on what constitutes permanent data loss when reviewing regulatory action(s) following a LockBit incident, given that law enforcement has provided advanced decryptor tools that were otherwise not available on a similar scale.
Forensic Evidence
It is common to state that 'there was no available forensic evidence' for an organisation to disclose to interested parties as result of encryption. However, with the release of comprehensive decryptors for past and current victims, it may change the convenient historic conclusion for LockBit breaches.
Reporting
With the NCA leading Operation Cronos, alongside the FBI, it shows an encouraging and clear example of why notifying and involving Action Fraud, the National Cyber Security Centre and the NCA from day one can lead to promising results. It is evident that practitioners' support of increased reporting to government agencies can only assist future victims of cyber-attacks.
[1] FBI: https://lockbitvictims.ic3.gov/
NCA: lockbit@nca.gov.uk
International: https://www.nomoreransom.org/en/decryption-tools.html